If you’re into the software development domain, you know how exciting it is to launch new software or a set of advanced features. However, along with this excitement, there is also a bit of concern about security vulnerabilities…
What if there is any design or coding glitch in the software?
What if the external library contains a hidden flaw?
What if there are any defects in the open-source components or third party code?
According to the National Vulnerability Database (NVD), in 2018, there were about 16,000 new vulnerabilities discovered and assigned a Common Vulnerabilities and Exposures (CVE) identifier. This is more than 50 per day!
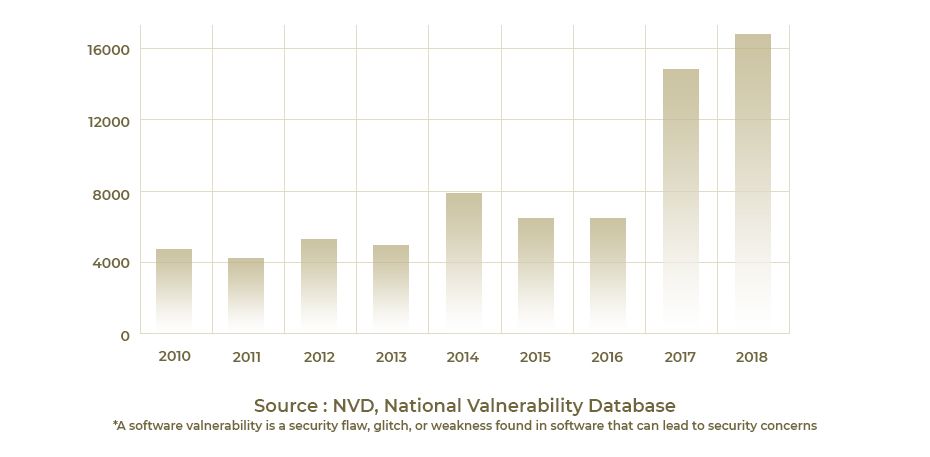
Explosion of Known Vulnerabilities
Although we’ve been able to elevate our software supply chain with the help of software development methodologies like Agile & DevOps, and through substantial automation of the software development life cycle (SDLC), we lag behind when it comes to its security.
In simple words, the increased speed of a modern CI/CD (continuous integration and continuous delivery) pipeline and the elimination of manual checks & fixes have posed the need for additional security measures.
This article discusses all you need to know about software supply chain and how DevSecOps can help you deal with the security issues associated with it.

Developing software is a tricky task!
To be honest, with so many parameters to work upon, it is almost impossible to develop bug-free software. However, there are actions that you can take to improve software quality and mitigate risk – like effectively securing your software supply chain.
For those who don’t have a clear understanding of what a software supply chain exactly is or how a typical software supply chain attack takes place, here’s a simplified explanation:
What is Software Supply Chain?
A software-focused supply chain is similar to the supply chain that exists in a typical manufacturing organization – You have your raw materials (i.e. pieces of code, third-party libraries, open-source components), which you assemble together and transport through a certain route (i.e. network) to the destination (i.e. software repository).
Eventually, the finished product (i.e. application) is delivered (i.e. deployed) to the end customer.
So, does the software supply chain end once the software gets deployed?
Unlike most tangible assets, the software supply chain doesn’t quite end after the software gets deployed.
You may release software updates, launch new versions, or gather customer feedback and improve accordingly. Moreover, you may also provide support and maintenance.
Make your software run smoothly without any anomalies.
Talk with one of our QA experts!
The Need for Software Supply Chain Security
IT infrastructure has evolved dramatically during the last decade. Still, there hasn’t been an equivalent enhancement in the security and compliance monitoring tools.
Due to this, most of such tools aren’t capable of testing as fast as a typical Agile or DevOps methodology demands. As a result, there has been a significant rise in software supply chain attacks.
What is a software supply chain attack?
It is an act of injecting malicious code straight into the source of a signed and trusted app. This app can then be distributed through legitimate software updates. The motive behind this act is to contaminate the trusted source and gain access to a huge cluster of trusting victims.
To give you a better understanding of how a software supply chain attack takes place, let’s discuss the current scenario:
Current scenario
Today, most of the software development projects involve the use of open source components or third-party libraries – if a code is readily available, why waste time rewriting it?
This is what exactly the attackers are waiting for you to do. They make use of the trust relationship (i.e. trust developed between you as a customer and the manufacturer/supplier of the third-party code) to deliver malware – they inject malicious code into the third-party code.
As you download and implement this third-party code, you become the victim.
Real-world examples
In 2017, Cisco discovered malware in a widely used system-cleaning tool, CCleaner, which infected over 2 million customers globally.
Another instance is the destructive malware “NotPetya,” which deployed a ransomware payload using a legitimate software package used by organizations in Ukraine and spread via legitimate software updates released by the vendor.
The above examples prove that security has not been embraced as effectively as required, and there is an increasing need for an efficient security mechanism.
Possible Solution
Introducing security checks at all the stages of the software supply chain can be one of the possible solutions.
A majority of the software development companies will agree to this, but very few would actually implement it. This is because infusing security measures often decelerate the application development lifecycle and reduce the pace at which software, its updates, and its fixes are released.
Fostering a dynamic environment is great, but at the same time it is crucial to incorporate best practices in security – practices that keep apps secure without decelerating their development lifecycle.
This is where DevSecOps steps in!
Integrate security in your software supply chain.
Talk with one of our QA experts!
A Brief about DevSecOps
Security is something that no one wants to compromise, still, organizations do not take it seriously until and unless there is a need to.
DevSecOps is all about establishing a culture which involves eliminating silos, promoting collaboration, implementing automation, identifying vulnerabilities early, and executing seamless CI/CD pipeline.
Here’s the definition of DevSecOps:
What is DevSecOps methodology?
It is the process of incorporating security at every stage of the app development lifecycle, right from the inception (i.e. planning) through to the production deployment and monitoring, in order to identify & eliminate security vulnerabilities as early as possible rather than after the app is released.
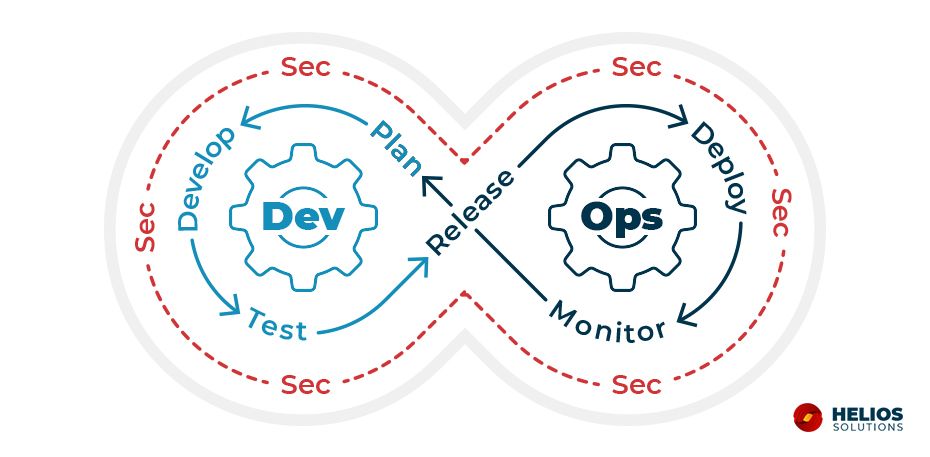
In a way, DevSecOps is the method to ensure a coherent balance between speed and security.
Using DevSecOps to Secure Software Supply Chain
When it comes to your software supply chain, a DevSecOps approach can help you secure it by uniting your app developers, security professionals, and IT operations personnel (i.e. DevSecOps team) and using their combined expertise to integrate security at every stage of the software supply chain:
1) Planning: Thinking beyond software specifications
From the very beginning of the software supply chain (i.e. the planning stage), the potential security issues should be taken into consideration. The DevSecOps team must think beyond user interface and product features – it should also focus on:
- Developing a comprehensive, documented security defense strategy; it must include information about which security tools to use and must address all the activities involved in software supply chain
- Creating an acceptance test criteria (understanding user’s response to an app’s functioning)
- Crafting a threat-defense model (getting a holistic view of IT security to identify threats, suspicious user activities, policy violations, and organizational data related risks)
2) Sourcing:
Here, the DevSecOps team must carry out check-driven sourcing:
- Check for compromised software building tools
- Check for compromised third-party or specialized code
- Check for pre-installed malware on components; utilize the latest versions of components
- Check for digital signatures
3) Building (and Testing):
At this stage, the DevSecOps team must follow the best practices of software coding and software quality assurance (testing includes front-end, back-end, API, and database):
- Maintain a highly secure build and update infrastructure
- Utilize CI/CD process
- Introduce secure API gateways
- Run automated tests and dependency checks at every stage
- Integrate vulnerability scanning into the CI/CD process; especially, check for vulnerabilities in Amazon Machine Images, Virtual Machines, Containers, and the OS (proactively removing the problematic components or dependencies)
4) Transporting:
Here, the DevSecOps team must design activities to protect the usability and integrity of the network (this includes both hardware and software):
- Manage access control
- Apply firewalls
- Use intrusion prevention systems
5) Deploying (and Monitoring):
If all of the above stages are completed successfully, and the app is ready to be deployed, the DevSecOps team must:
- Monitor the app performance and user experience
- Automate configuration management
- Provision the runtime environment
- If possible, develop an incident response process for supply chain attacks
In addition to integrating security at every stage of the software supply chain, a DevSecOps approach also includes training activities i.e. training about automation and collaboration with the motive to develop & deliver faster and secure better.
DevSecOps isn’t an option, it’s a necessity!
Almost daily reports about cyber-attacks, security holes, and data losses prove again and again how important security is today. Organizations need to be active in their approach to implementing security measures. Adopting the DevSecOps culture is the way they can put security at the forefront of their software supply chain activities and develop apps that don’t have any weak fence around them.
Need help with secure software development services?
Talk with one of our software development experts!



