With enterprise mobility becoming a greater area of focus in organizations, we have seen a huge surge in cloud computing and Bring Your Own Device (BYOD) culture across industries. Besides increasing employee satisfaction and convenience, these apps and devices also bring in security and access related issues. Hence, maintaining and managing them is becoming a daunting task for Enterprise IT.

The year 2017 was essentially dominated by enterprise mobility solutions influenced by artificial intelligence, augmented reality and Internet of Things (IoT). As this trend continues to rise in popularity, enterprise mobile app deployment is gaining momentum in 2018 as well.
Businesses are more than willing to invest in enterprise mobility solutions as is evident from the recent survey that shows that 71% of enterprises consider mobility as a top priority to stay ahead of the curve.
Even though enterprise mobility solutions have far-reaching implications and have been shaping the face of the business landscape over the years, they have their share of challenges too.
Are you facing enterprise mobility challenges?
Get consultation from our IT experts.
Challenges for enterprise mobility
Although enterprise mobility plays a pivotal role in improving organizational processes, customer service, employee performance and other key aspects of your business, it also brings in issues that you need to consider for achieving ROI and maintaining a positive environment at workplace.
Here are three main pain points that organizations need to address in order to harness the benefits of enterprise mobility: 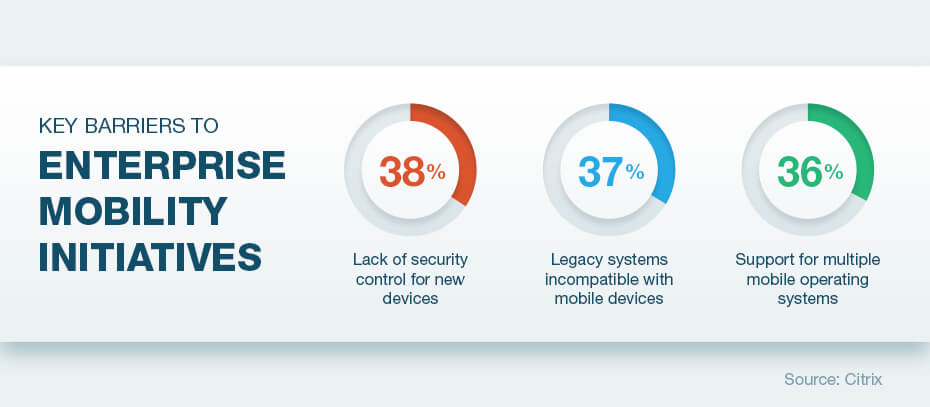
Multiple mobile OS support
The rise of BYOD culture in business has been posing a significant challenge to the mobility programmes of organizations in the form of unsupported devices and operating systems. However, an effective enterprise mobility management (EMM) solution could make it relatively easier for companies to manage diverse mobile operating systems. Moreover, deploying updates or patches and improvements will also be convenient irrespective of the operating systems.
Legacy systems impeding mobility
 Organizations wherein legacy systems have already become an inherent part of their daily operations won’t be able to rip apart those age-old systems in a single stroke for embracing processes that enable mobility.
Organizations wherein legacy systems have already become an inherent part of their daily operations won’t be able to rip apart those age-old systems in a single stroke for embracing processes that enable mobility.
On the other hand, they would need to either upgrade those legacy systems or create an intermediate system to enable processes that lead to enterprise mobility.
Another option could be, changing or removing the legacy systems that hinder mobility initiatives and establish new systems altogether.
Whatever option or combination of options you decide to work on, it will basically depend on the ROI that you think can be achieved from the system that enables mobility.
Mobile security
 Research reveals that more than forty percent of enterprises do not have a dedicated budget for mobile security efforts. When users bring their personal devices to work and tether them to laptops or other corporate devices via wireless hotspot, they are actually putting corporate data and information at risk.
Research reveals that more than forty percent of enterprises do not have a dedicated budget for mobile security efforts. When users bring their personal devices to work and tether them to laptops or other corporate devices via wireless hotspot, they are actually putting corporate data and information at risk.
You need to manage, analyze and control the plethora of devices, applications and content in order to ensure the security of corporate data. To achieve that, our IT strategy consultants recommend having a comprehensive EMM strategy. What is an EMM? Let’s take a look!
What is an enterprise mobility management solution?
Enterprise mobility management solution is a set of policy and configuration management technologies designed to secure corporate data on employees via device, application and content management. 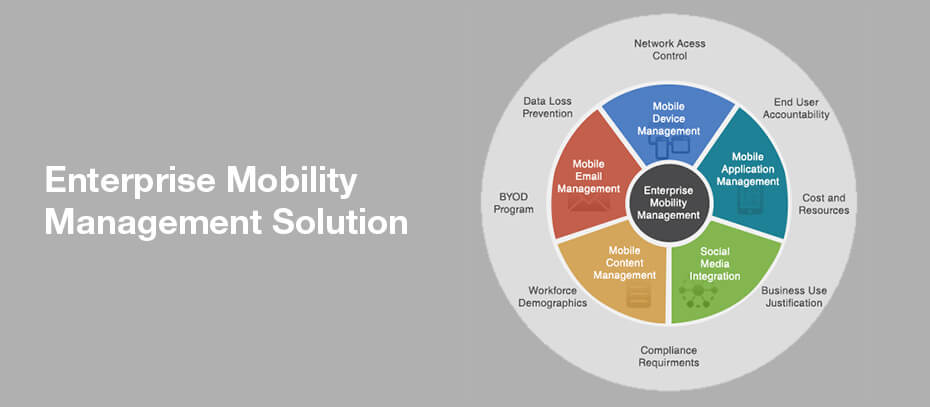 As each business is unique, so are their needs for mobility management. What works for others might be inadequate for your organization. Therefore, an organization would need to tailor its EMM solution based on its specific requirements.
As each business is unique, so are their needs for mobility management. What works for others might be inadequate for your organization. Therefore, an organization would need to tailor its EMM solution based on its specific requirements.
This would enable them to effectively leverage the full potential of enterprise mobility and at the same time maintain security policies.
Get an EMM solution tailored to your business needs
Talk to our IT strategy consultants now!
Mobile Device Management (MDM)

MDM technologies enable you to remotely manage the lifecycle of mobile devices and their respective operating systems. With MDM, you can install unique profiles on mobile devices and remotely control and enforce policies through them. For instance, if any device is stolen or lost, you can wipe out all the apps and data thus preventing them from getting compromised.
If you are looking for an EMM solution of this type then get in touch with us and we would develop a solution tailored to your specific needs.
Mobile Application Management (MAM)
 MAM is another flavor of EMM that allows you to manage mobile applications rather than hardware. It covers deployment as well as updating of mobile apps including license management and support for push notifications.
MAM is another flavor of EMM that allows you to manage mobile applications rather than hardware. It covers deployment as well as updating of mobile apps including license management and support for push notifications.
MAM also allows you to apply security policies to apps and remove them and any associated data selectively from a device. Thus, corporate data can be protected without having to wipe out all the applications from a device. Hence, this EMM solution is gaining popularity among organizations practicing BYOD policies.
Mobile Content Management (MCM)
 MCM tools enable you to access content on mobile devices while maintaining content security, content push and protection of files. You can also enforce authentication policies on MCM platforms and at the same time integrate it with enterprise services from Google, Microsoft and others to access files and other data on authorization.
MCM tools enable you to access content on mobile devices while maintaining content security, content push and protection of files. You can also enforce authentication policies on MCM platforms and at the same time integrate it with enterprise services from Google, Microsoft and others to access files and other data on authorization.
Wrapping up
As already discussed, there is no one size fits all platform when it comes to enterprise mobility management solution. An EMM solution can help your organization to become more agile and at the same time minimize employee workload. Besides, it would help to you to harness the benefits of workforce mobility without putting corporate information at risk.
Want to find out which EMM solution aligns best to your business needs? Reach out to our experts for consultation and substantially reap the benefits of enterprise mobility. Collaborate with us for developing enterprise mobility solutions for a smarter work approach and also consider investing in EMM solution to best protect your digital assets.



