Containers have revolutionized the way we think about application development, shipment and deployment, and also the pace at which DevSecOps teams can respond to business requirements.
According to 2019 Container Adoption Survey (carried out by Portworx and Aqua Security), a whopping 87% of IT pros said that they were running container technologies.
With more and more organizations migrating their workloads to containers, orchestration platforms like Kubernetes, Docker Swarm, Apache Mesos and Amazon Elastic Container Service (ECS) have become a crucial part of the container ecosystem.
For those who don’t have a clear idea of what a container orchestration tool exactly is, it’s the tool that automates the tasks required to run a containerized application “at scale”. This includes container deployment, container-to-container communications, and load balancing across nodes (i.e. clusters of host servers).
Talking about Kubernetes (or K8s), it has become the de facto standard platform for container orchestration – majority of organizations are running containers using K8s to some extent.
However, working with Kubernetes environment is challenging. One of the key reasons behind this is that it brings a whole new set of security concerns. Organizations need to address them to get the best out of K8s.
This article discusses everything you need to know about Kubernetes security along with the best practices to address the security concerns.

Kubernetes has rapidly become a key element in cloud native infrastructure implementation and DevOps software development. It has allowed organizations to run containers “at the edge”.
As a matter of fact, without a container orchestration tool like K8s, it would not have been feasible to run a containerized application (for production purposes) as manually deploying and managing containers requires too much of time and attention.
According to a survey conducted by Rancher Labs, Kubernetes has emerged as the dominant technology standard for container management with 90% of respondents using it for orchestration.
According to a survey carried out by StackRox, 87% of organizations are managing some portion of their container workloads using Kubernetes.
In addition to K8s’ increased usage, the survey carried out by StackRox also reveals that 94% of organizations have experienced security issues (over the past year) in their container environment.
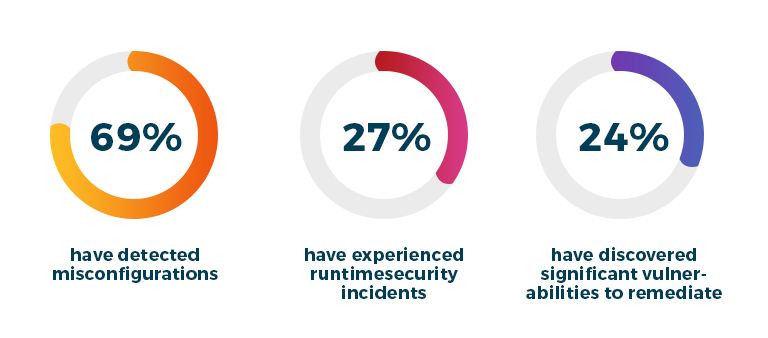
K8s security might seem simple, but is actually a bit complicated.
Build and deploy modern cloud-native apps using Docker and K8s
Talk with one of our solution architects
Kubernetes Security
K8s is awesome at automating many of the tedious tasks required to deploy containerized applications, but it lags behind when it comes to managing security.
It has very limited features that can help you secure a containerized application. For example, it can impose Role-Based Access Control (RBAC) policies, place restrictions on how containers and pods behave, and encrypt network traffic using Transport Layer Security (TLS).
Outside these basic security measures, K8s doesn’t offer much – it doesn’t inspect container’s contents for known security flaws, doesn’t detect any abnormal behaviour within a containerized application, and doesn’t strengthen networks against attack.
What is Kubernetes Security?
K8s security is all about establishing and implementing security measures to protect container-based applications from potential threats and attacks. These attacks include exploitation of vulnerabilities in container base images and third-party libraries, unauthorised administrative access, and cluster misconfigurations that facilitate malicious activities.
Kubernetes Security Issues
Creating and maintaining a secure Kubernetes native infrastructure is not easy. It involves addressing the security challenges associated with each component involved in the environment.
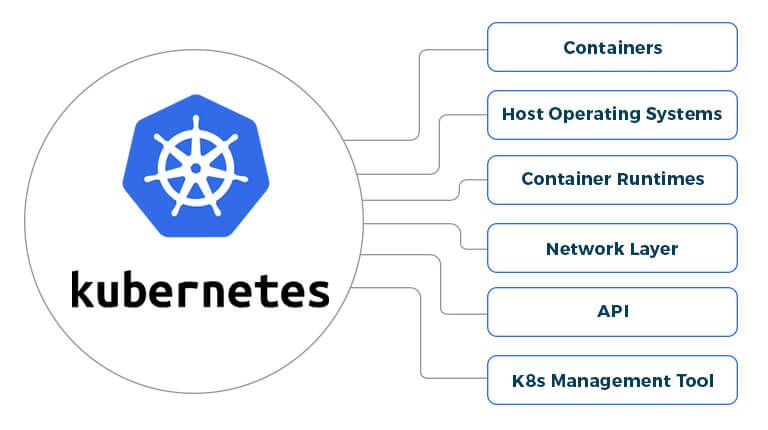
Containers
Containers are vulnerable in a number of ways. For instance, poorly configured images can allow a hacker to break into an enterprise network. Also, images may contain authentication keys or certificates that hackers can use in further attacks.
Host Operating Systems
The OSs installed on K8s nodes can have vulnerabilities or malicious code. This can offer hackers a straight path to Kubernetes clusters.
Container Runtimes
K8s supports an array of container runtimes which could potentially contain vulnerabilities that allow hackers to take control of individual containers, deepen attacks from one container to another, and even gain access of the K8s environment itself.
Network Layer
K8s counts on internal networks to establish communication between nodes, pods, and containers. Furthermore, it also exposes applications to public networks so that they can be accessed over the Internet. Both network layers could allow hackers to gain control over the cluster or intensify attacks from one part of the cluster into others.
API
The Kubernetes API service acts as the front door to any cluster. It is normally exposed on every deployment, since it’s required for management purposes. As it plays a central role in allowing components to communicate and applying configurations, it could contain vulnerabilities or misconfigurations that permit attacks.
Kubernetes Management Tools
K8s management tools such as Kubernetes Dashboard, Kubectl, and Kubectx could be subject to vulnerabilities that facilitate abuse on a Kubernetes cluster.
Now that you know about K8s security issues, let’s check out the Kubernetes security best practices that can help you secure K8s native infrastructure.
Leverage the benefits of the de facto container orchestration tool
Get in touch with one of our K8s architects
Kubernetes Security Best Practices
As the built-in security features of K8s are limited, it’s vital for DevOps teams to take appropriate steps to secure their clusters. Here are some of the best practices:
1) Configure Pod Security Policy
2) Define Network Policy
3) Strengthen Host Security
4) Manage Runtime Security
5) Monitor Kubernetes Environment
6) Separate Sensitive Workloads
7) Consider Security Tools
1) Configure Pod Security Policy
A PodSecurityPolicy (PSP) is a set of guidelines that define how pods in a cluster should communicate, and also ensure that only authorized pods run in the cluster.
It is important for you to make sure that you establish and enforce the pod security policy in a way that prevent pods from running with root privileges, restrict containers in pods from running as the root user, prevent pods from getting into host ports, and restrict volume type access.
2) Define Kubernetes Network Policy
K8s by default exposes a few ports; and so, such ports should be restricted from anonymous access. Moreover, unused ports should not be exposed, and where non-authenticated services are used, restrict access to whitelisted sources.
You need to define a network policy that addresses the points like what network traffic is allowed for a cluster, network segmentations and guidelines, and encryption procedures.
3) Strengthen Kubernetes Host Security
Kubernetes environment as secure as the server that hosts it.
With different architectures of K8s host servers available, there is no one-size-fits-all approach for K8s host security, and in some cases you have more control over security settings on the host than in others.
In order to enhance K8s host security, you need to make sure that a you’re running a security- solidifying framework, utilizing role-based access control to establish necessary access rights to the K8s environment and any resources it uses, and most importantly minimizing network connections.
4) Manage Kubernetes Runtime Security
Container-specific runtime used along with K8s is not immune to security vulnerabilities – K8s won’t do anything to detect breaches that abuse the runtime or known security vulnerabilities within the runtime.
If you want to mitigate risks and manage vulnerabilities effectively, you need to keep the runtime up-to-date.
5) Monitor Kubernetes Environment
Collecting and monitoring metrics from your Kubernetes environment can provide you with crucial insights and early warning about possible attacks/breaches.
For instance, if you observe an unusual uptick in the network activity, or a sudden change in the number of container instances you are running, that could possibly indicate an intrusion attempt.
Most of the cloud computing services providers — such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) — have started to provide advanced features to the businesses to effectively monitor and manage their Kubernetes environment.
6) Separate Sensitive Workloads
To avoid the potential impact of a compromise, it’s better to run sensitive workloads on a dedicated set of machines.
This tactic minimizes the risk of a sensitive application being accessed through a less-secure application that shares a container runtime or host.
7) Consider Kubernetes Security Tools
As discusses previously, K8s offers only the basic security measures, leaving the advanced security monitoring and compliance enforcement for administrators to manage.
However, there are a number of third-party tools available that can help secure K8s stack effectively. Some of the advanced K8s security tools include: Kube-Bench, Twistlock, Kube-Hunter, and Project Calico.
Bottomline
K8s is an awesome container orchestration tool but not a great security tool. Keeping it secure requires you to take extra care on multiple fronts by following DevOps principles and some of the best security practices — from configuring pod and network security policies to strengthening host and runtime safeties to monitoring K8s environment and separating sensitive workloads.
The approach that you undertake to accomplish each of the above tasks varies based on your specific IT architecture, but the fundamental thing is to remember that you need to care a little extra, because when it comes to security K8s doesn’t do much.
Deploy and manage containerized apps at scale through K8s
Talk with one of our K8s architects



